Git Security
- Code Reviews, Two-person reviewed
- Git Commit Signing
- MFA on accounts, GitHub, Gitlab etc.
Reading Material
Git Commit Signing Exercise
Needed:
- GPG Key
- GitHub Account
Generating a GPG Key
- Generate a key with gpg
gpg --passphrase '' --gen-key - Select what key you want to use
- Fill out your name and your email address. Make sure this matches the one in your GitHub account.
- Add a comment if you want to remind you what the key is for.
- You may be prompted for a passphrase to add to the key for extra security, for this example hit enter 3 times to not add a passphrase.
Here is what the prompts will look like.
Add Key to GitHub Account
1. Export public key
Get the Key ID with gpg --list-secret-keys --keyid-format LONG $YOUR_EMAIL
Export the public key with gpg --armor --export $YOUR_LONG_KEY_ID
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEYRwLhBYJKwYBBAHaRw8BAQdAsQbWuqV2P5y1HXlkoFTM9qyrypc+zB9YO/fI
DYAjZ6C0PkphbWVzIFN0cm9uZyAodGVzdGluZyBmb3Igd29ya3Nob3ApIDxzdHJv
bmcuamFtZXMuZUBnbWFpbC5jb20+iJQEExYKADwWIQQ+BCSTEkbTOoaJC8eCRqHs
kAteMAUCYRwLhAIbAwULCQgHAgMiAgEGFQoJCAsCBBYCAwECHgcCF4AACgkQgkah
7JALXjDeKgEA1JtsGyIEg8ZUANvkbJfdNEs2e1Ns/M3PcRYMUxc1yugA/3tHEDJb
Fw+QghwzcHXWsqlkAmj5TZglHyfYsbwlgzoLuDgEYRwLhBIKKwYBBAGXVQEFAQEH
QGg2S81eJftEiG4AeiKC3D6H94y1ifSuTZ6BBofcilsTAwEIB4h4BBgWCgAgFiEE
PgQkkxJG0zqGiQvHgkah7JALXjAFAmEcC4QCGwwACgkQgkah7JALXjCVgwD+Ob4+
fG5zzmP/Hg13SFsxLZc+5EKrxHJ1z+bNQQ5ARxYBANbOuPnxLtPL4eY4TqIY0k1X
8HmXv9JXEwMHLYiN4fwF
=03gp
-----END PGP PUBLIC KEY BLOCK-----
2. Add to GitHub
Open https://github.com/settings/keys
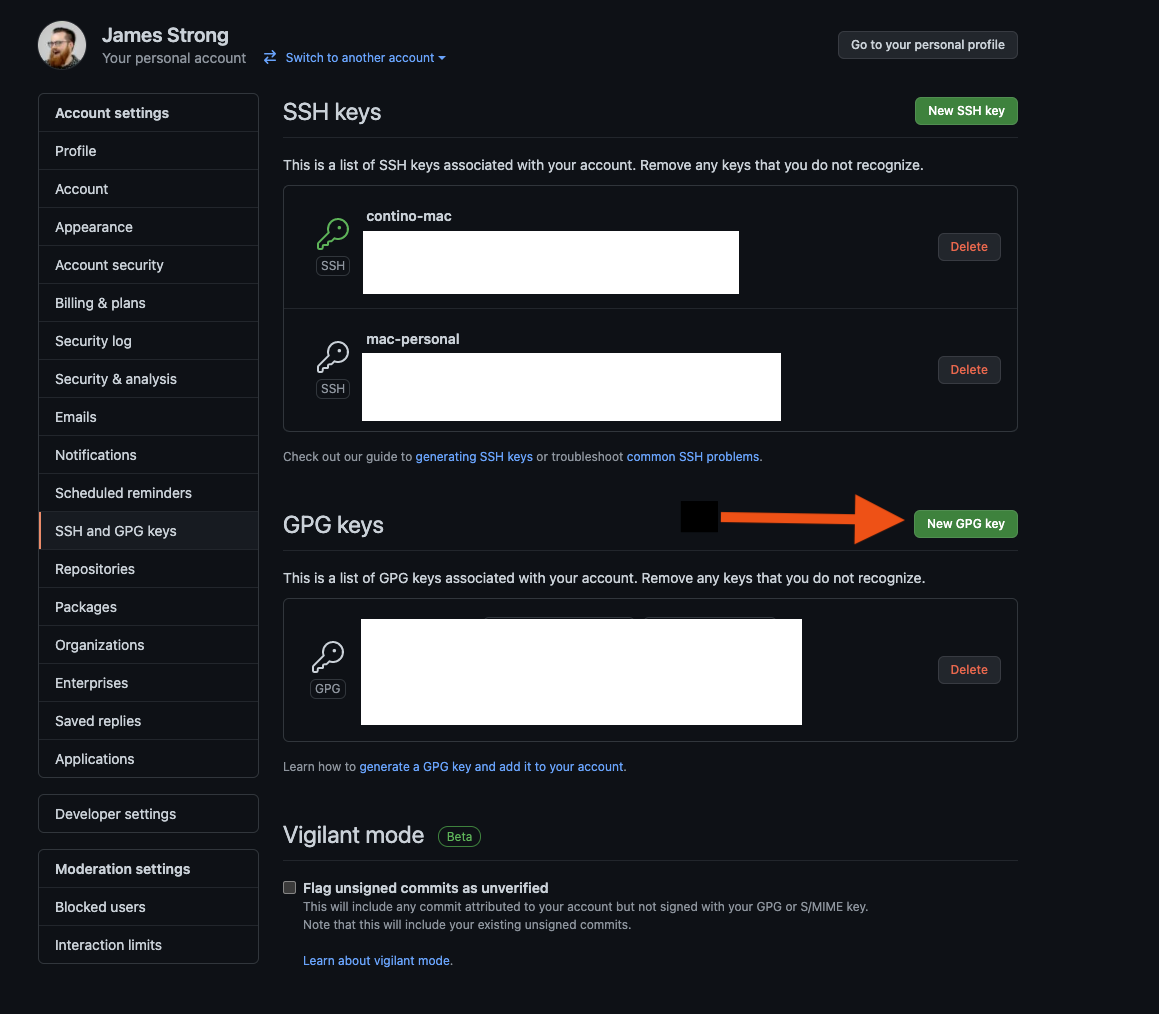
Copy and Paste the Public Key into your GitHub account
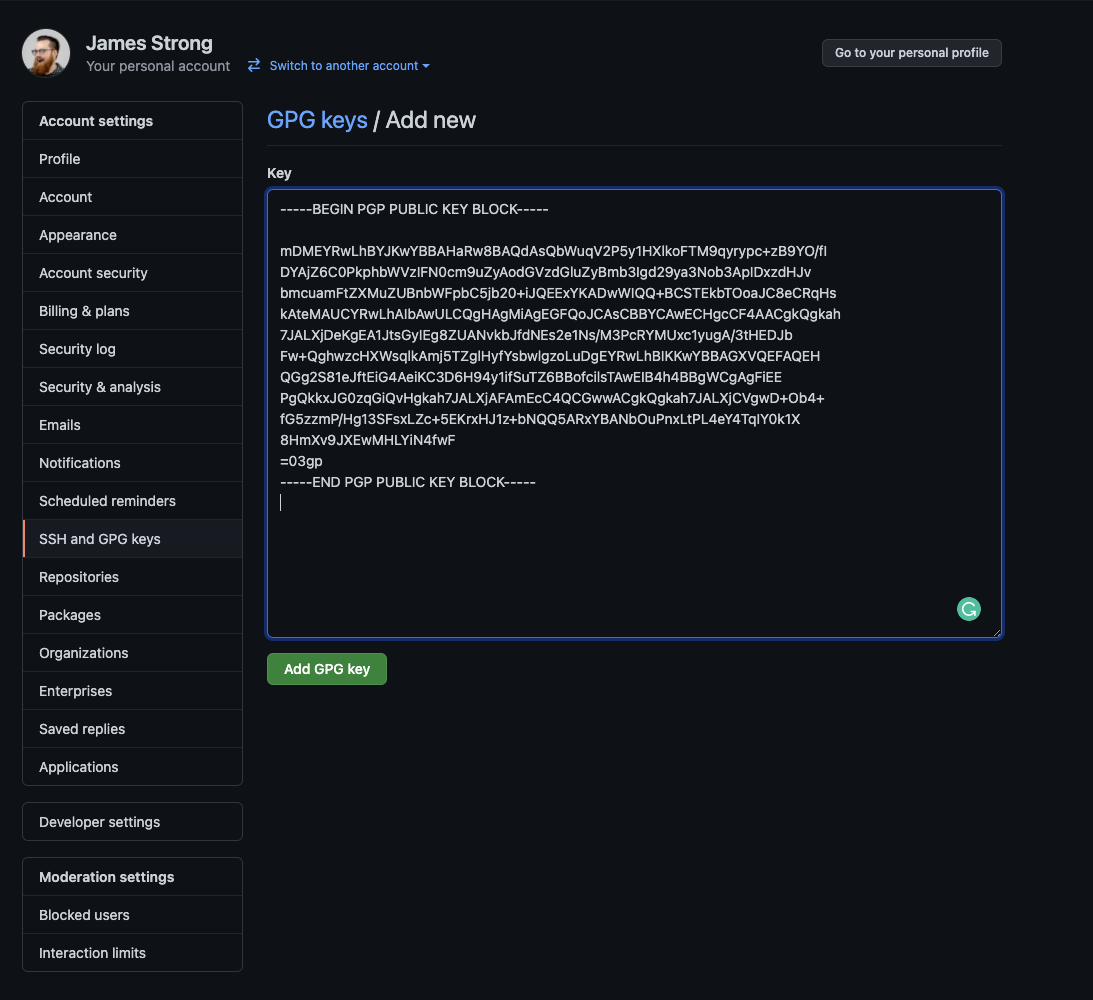
3. Add to git config
Get the key id for the one we just created.
$ gpg --list-secret-keys --keyid-format LONG $EMAIL
sec ed25519/8246A1EC900B5E30 2021-08-17 [SC]
3E0424931246D33A86890BC78246A1EC900B5E30
uid [ultimate] James Strong (testing for workshop) <strong.james.e@gmail.com>
ssb cv25519/0BAFF11345FB8338 2021-08-17 [E]
Update git config to use the key.
$ git config --global user.signingkey 3E0424931246D33A86890BC78246A1EC900B5E30
$ git config --global commit.gpgsign true
4. Test a Commit.
Create a testing repo in GitHub.com, then add it locally
cd ~/environment/
mkdir signing-test
git init
Initialized empty Git repository in /home/ec2-user/environment/signing-test/.git/
echo "signing-test" >> README.md
Then use those remotes to add to empty repo.
git remote add origin git@github.com:strongjz/git-signging-test.git
git branch -M main
git push -u origin main
git add -A
git commit -m "signing"
[main b2a6fb5] signing
git push origin main
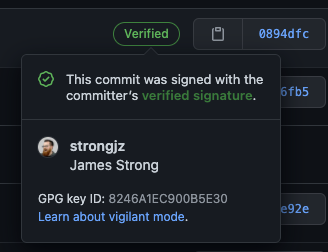
5. Verify in GitHub
In the commit history you can see a “Verified” tag on your commits now
Make sure to store this GPG private key in a secure location
6. Store GPG key (optional)
To export the key use this.
Identify your private key: gpg --list-secret-keys $EMAIL
sec ed25519 2021-08-17 [SC]
3E0424931246D33A86890BC78246A1EC900B5E30
uid [ultimate] James Strong (testing for workshop) <strong.james.e@gmail.com>
ssb cv25519 2021-08-17 [E]
Run this command to export your key: gpg --export-secret-keys 3E0424931246D33A86890BC78246A1EC900B5E30 > private.key
If you have a passphrase on the key you’ll have to enter it to export it.
Copy the key file to another secure location.
To import on a new machine, run gpg --import private.key
Sources:
Using Keybase: https://github.com/pstadler/keybase-gpg-github